Introduction
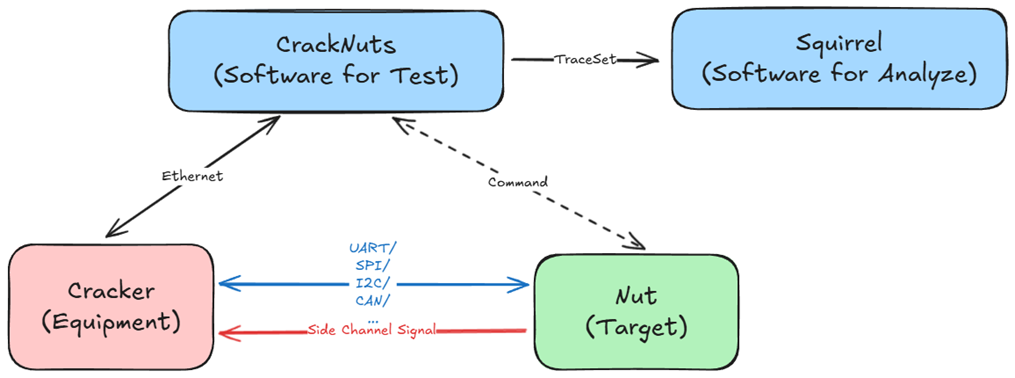
The Cracknuts project aims to provide users with a "professional, easy-to-use, open-source" chip security analysis solution. It enables power analysis and electromagnetic analysis on various target chips, and can perform clock glitching and voltage glitching fault injection attacks. All software and hardware code of the project will be open-sourced, facilitating user customization and integration.
Components
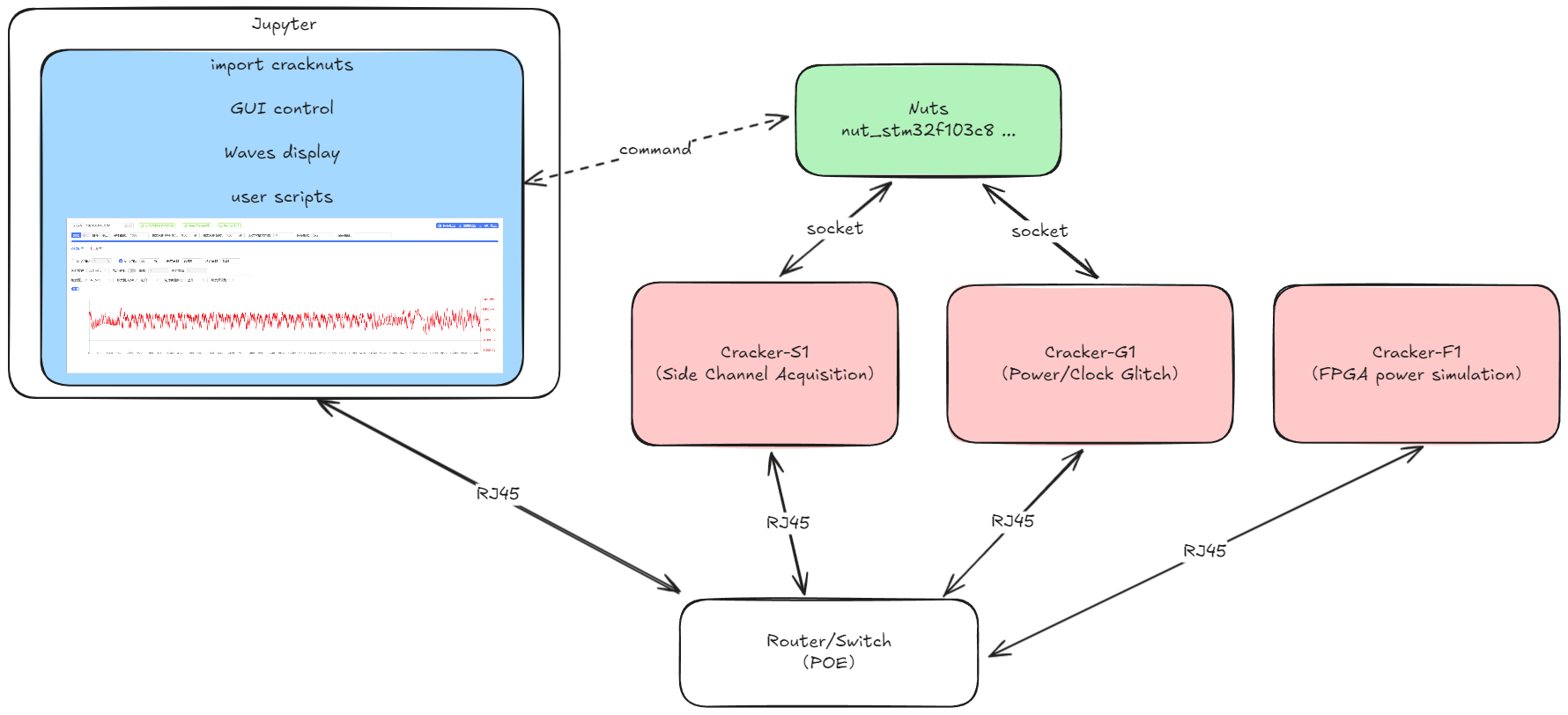
The project consists of three parts: the CrackNuts analysis software, the Cracker testing device, and the Nuts test targets.
CrackNutsusesJupyteras the development environment.- Supports device and waveform display interface
- Provides convenient and easy-to-use API interfaces
- Cross-platform:
Windows,Linux,Mac
Crackerincludes a series of testing devices, capable of analyzing the security of variousNutsCracker-S1: Primarily used for side-channel analysisCracker-G1: Primarily used for fault analysis (under development)Cracker-F1: Primarily used for hardware design side-channel security verification (under development)- More testing devices will be developed based on user requirements ...
Nutsincludes a series of target chips (custom development available upon user request)Nut-stm32f103Nut-stm32f4- More test devices will be developed based on user requirements ...
Deployment
All Cracker devices support POE (Power over Ethernet) operation, offering the following advantages:
- Greatly simplifies deployment—only one network cable is required for both power supply and communication
- Breaks physical distance limitations, enabling remote testing
- Facilitates networking, allowing simultaneous control of multiple testing devices